Did you know in 2022, the total damage incurred by cyberattacks reached $6 trillion.? In recent years, cyberattacks are on rampant. Organizations have turned to Vulnerability Assessment and Penetration Testing (VAPT) to find and manage security flaws in response to the rise in cyberattacks and the sophistication of malware and hacking techniques. A penetration test, also known as VAPT, simulates a hacker attack on an IT infrastructure to determine its general security.
VAPT testing provides comprehensive reports on how a hacker can bypass a system’s current security measures by assessing its vulnerabilities.
What is Vulnerability Assessment and Penetration Testing (VAPT)?
Vulnerability assessment and penetration testing techniques are used by organizations to assess the security of their IT networks and applications (VAPT). A VAPT audit examines a system’s overall security by thoroughly inspecting its components.
A VAPT audit aims to identify any software flaws that hackers may exploit. Therefore, VAPT security audits are performed using a methodical process incorporating several tools, techniques, and methodologies.
Why is the VAPT audit important for your organization?
In any industry your organization is in, vulnerability assessment and penetration testing services are necessary. It involves confirming and evaluating your organization’s security position.
Your business’s security is determined based on whether it is protected from external attacks. We hear a lot about hacking problems and cyber-attacks these days. All of us must protect our systems and networks. Vulnerability assessments and penetration tests are helpful tools for identifying attacks and security flaws.
Additionally, VAPT testing supports data security compliance for securing customer data stored in networks and applications against hacker attempts to compromise it.
How Can Data Breach Affect Your Organization?
A computer system or network’s weaknesses or vulnerabilities are found through a vulnerability assessment, also known as a vulnerability scan. A vulnerability assessment aims to identify the system’s vulnerabilities and assist the system operator in addressing them.
Either manually or automatically, performing the assessment is an option. If manual testing is used, the tester will use an evaluation process to find the vulnerabilities. An automated vulnerability assessment can be employed if the manual evaluation needs to be more sufficient or shorter.
A penetration test also called a pen test, is a legitimate simulated attack on a computer system to assess the system’s security. It is a type of “security audit” but indicates a degree of aggression that goes beyond standard audit methods.
Penetration tests are carried out with the system owner’s knowledge and approval. These tests are usually carried out to identify security flaws before criminals or unethical hackers do.
How does VAPT defend against Data Breaches?
Data breaches are a severe issue for all businesses and organizations, not just those who experience a hack. Data breaches can come from identity theft, money theft, and diminished user trust. However, data is the asset any business has the most exposure to risk.
Organizations must make sure that their data is safeguarded and kept secure. Vulnerability assessments play a role in providing a certain amount of security against data theft. One of the best ways to guarantee the safety of your network and data from potential attacks by malevolent hackers is through vulnerability assessments.
A critical phase in the vulnerability management process, vulnerability assessment is a technique for identifying known security flaws in a system or network.
What are the Types of Penetration Tests?
The word “penetration testing” is general and has different kinds. Let’s examine a few of them in greater detail:
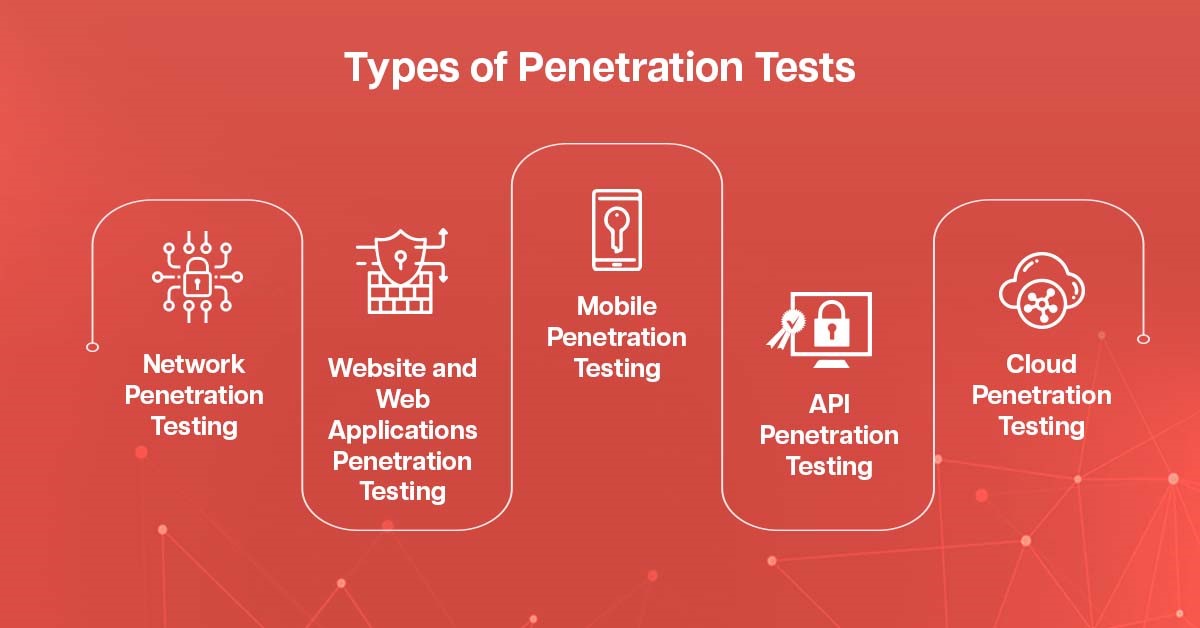
1. Network Penetration Testing
Network security is examined by network penetration testing, a type of security audit. It is one of the best ways to safeguard the sensitive data and information you keep and move across the network and identify and stop prospective and actual cyber-attacks and breaches
The goal is to attempt a system break-in by simulating a cyber-attack. Network penetration testing is the most reliable method for protecting sensitive data and information stored on the network and detecting possible and actual cyber-attacks and hacks.
2. Website and Web Applications Penetration Testing
The process of web application penetration testing is used to evaluate the website’s security. It is used to determine a website’s or its web applications’ vulnerabilities. Both white hat and black hat uses are possible.
Web application penetration testing aims to identify website security weaknesses before criminal hackers do. Penetration testing is typically used to determine the website’s security flaws, which are subsequently reported to the relevant team.
3. Mobile Penetration Testing
The technique of checking a mobile application for security flaws is known as penetration testing. This procedure is carried out to ensure that the applications are not disclosing private data to a third party. It is an important stage because even a tiny fault in the system may cost a business a lot of money.

Penetration testing for mobile applications covers a wide range of mobile applications, including:
Android application testing for vulnerabilities, iOS Penetration Testing for PWA, hybrid, and iOS applications
4. API Penetration Testing
An essential component of every business’s security infrastructure is API penetration testing. The potential of a breach is a bigger worry than ever before as a company’s data and infrastructure are increasingly exposed to the internet. But APIs pose a significant danger to the integrity of a company’s internal infrastructure and are a single point of failure.
Most businesses have a range of APIs that let staff members and applications from outside the company use internal tools, data, and infrastructure. These APIs have the potential to be misused to propagate malware, steal data, and
5. Cloud Penetration Testing
Security testing, known as “cloud penetration testing,” examines a cloud computing system for weaknesses that criminals might use.
A cloud provider’s security controls and procedures are tested through cloud penetration testing to see if they can fend off attacks and test the security of cloud computing systems. These checks should be carried out before a corporation moves its apps and data to the cloud and periodically as part of a cloud provider’s security upkeep.
As part of a corporation’s evaluation of the security of its cloud infrastructure, a third-party security company will probably conduct a cloud penetration test.
How often should you conduct VAPT?
Finding security flaws in your website is the process of using VAPT security. There are several factors to consider when determining how frequently a VAPT should be performed.
Among the most crucial elements are the following:
- How many flaws will a VAPT uncover?
- How long will the VAPT last?
- How much will a VAPT cost?
- What kind of information is being kept?
- Compliance Requirements?
However, as a general rule of thumb, you should check for vulnerabilities in your network, website, and web applications at least twice a year.
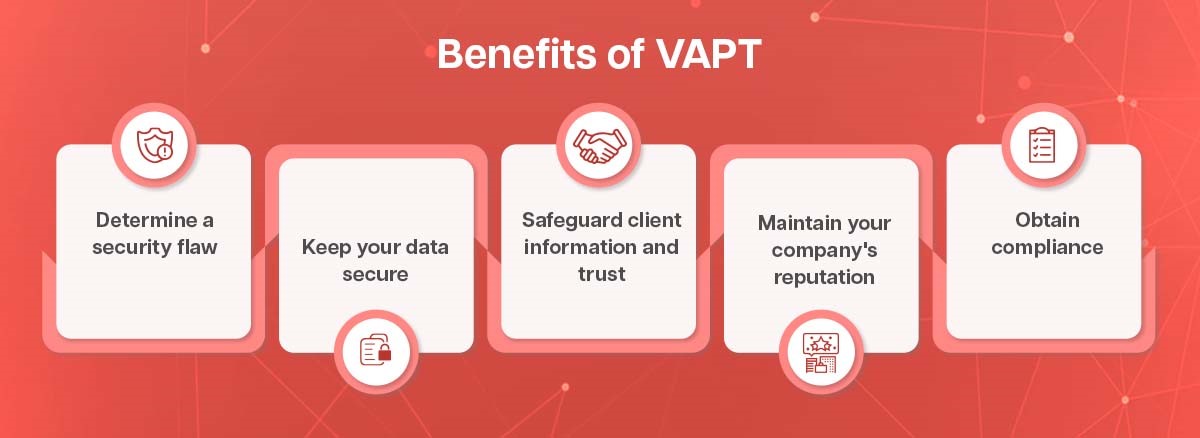
What are the benefits of VAPT?
The security of enterprise systems is a significant problem for every business. This is so because no company can afford a security lapse that can result in monetary loss or a damaged reputation. Therefore, an evaluation of the security vulnerability and penetration testing are the two methods for addressing it.
Here are the benefits of VAPT testing:
- Determine a security flaw
- Keep your data secure.
- Safeguard client information and trust
- Maintain your company’s reputation
- Obtain compliance
How to choose a VAPT provider/solution?
When deciding which Service is ideal for you, there are many things to consider. Price, features, and other factors are not the only considerations. You should consider the long term, the short term, the future, and the present.
Most of the time, the best provider is someone you feel comfortable with and can trust. But there are other elements. To find the ideal one for you by giving it some thought.
Here are a few considerations to make your decision about a VAPT service easier.
- Cost of the VAPT solution
- If the VAPT is performed by CERT-in empanelled agency
- The expertise of the VAPT Service provider
How SPOCHUB’s Solution helps you with your Website and Web Application VAPT?
SPOCHUB’s vVAPT identifies the weaknesses of the organization’s web application. With CERT-in Certification, SPOCHUB vVAPT services include a thorough security audit of Web applications. This is followed by routine VTMScan vulnerability detection.
SPOCHUB provides vVAPT Service in two stages:
1. Web application security audit performed by a CERT-in empanelled agency.
2. VTMScan annual website scanning service based on the chosen plan.
What are the benefits of choosing SPOCHUB’s vVAPT Service?
Our team of security professionals has created the SPOCHUB vVAPT service specifically for enterprises, giving them a straightforward digital certification process with a full year of security assurance. Here are some of the best benefits of our vVAPT Service.
- Assessment Report
We will give you a thorough security evaluation report with suggested corrective actions. The data enables you to find security flaws in your website and online applications so you can proactively fix any issues as they arise.
- Security Audit as per OWASP Standard
OWASP (Open Web Application Security Project) is the standard used for Web Application Testing that represents the 10 most critical application security flaws.
- Regulatory Compliance
After performing patch verification, show clients and stakeholders your dedication to security. Maintain compliance with the many regulatory bodies, like PCI DSS, ISO 27001, and GDPR, that call for regular application testing.
- Audit by CERT-In empanelled
We guarantee that qualified CERT-In empanelled auditor Security Brigade will carry out your assessments.
- Certificate for Safe-to-Host
To prove that your website is safe to host and that its users are protected from online assaults, we provide a safe-to-host certificate.
- Effortless online method
SPOCHUB offers Virtual VAPT service, which means you can become CERT-in certified in a matter of clicks.
Companies are scrambling to find new data protection methods as the frequency of data breaches increases. There is a wealth of information on the internet on data protection measures that businesses can take. However, the fact is that in order to protect their data, companies of all sizes must use a top-notch VAPT solution. In our blog post, we’ve discussed the value of a VAPT solution and how it can shield your company from malicious attacks. The nicest aspect is that all businesses can afford SPOCHUB’s vVAPT Service. Just get in touch with us here.


